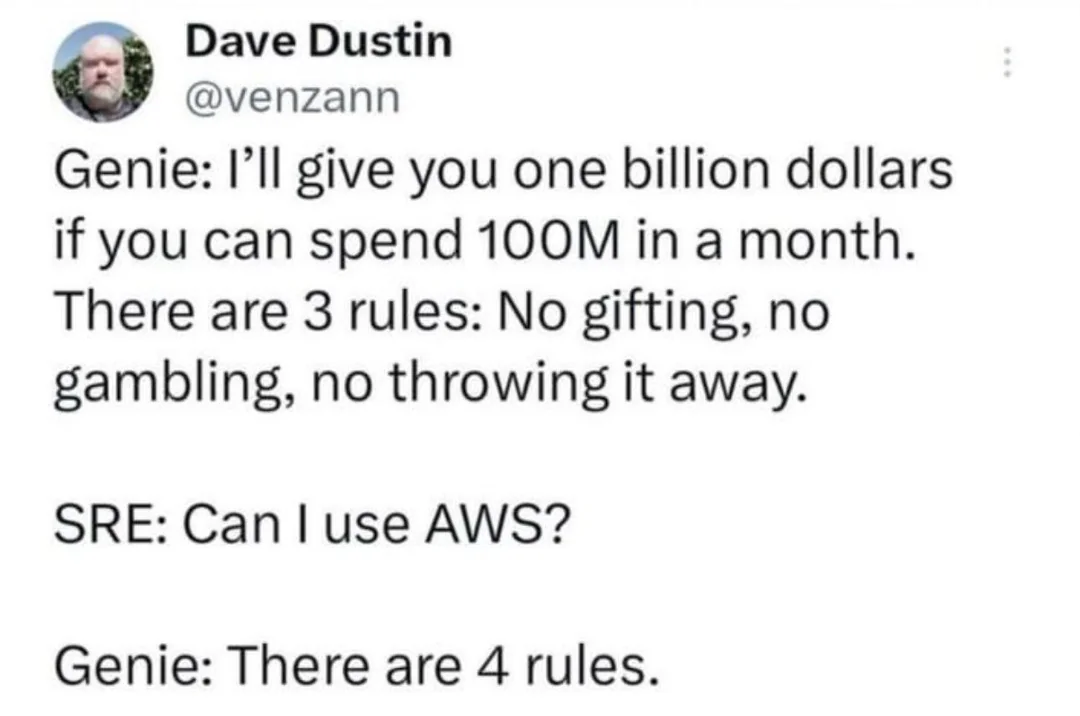
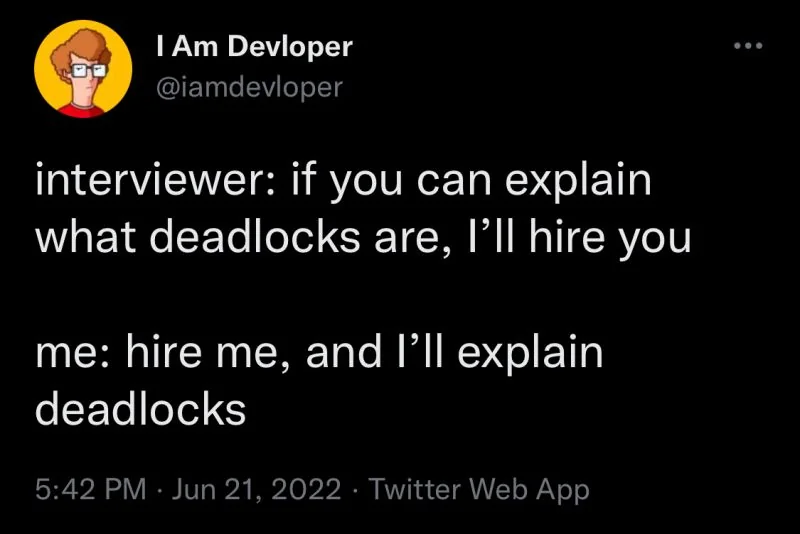
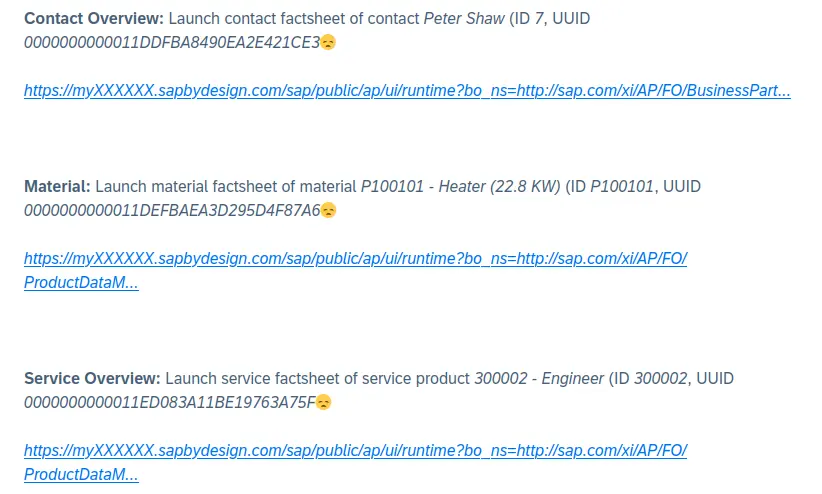
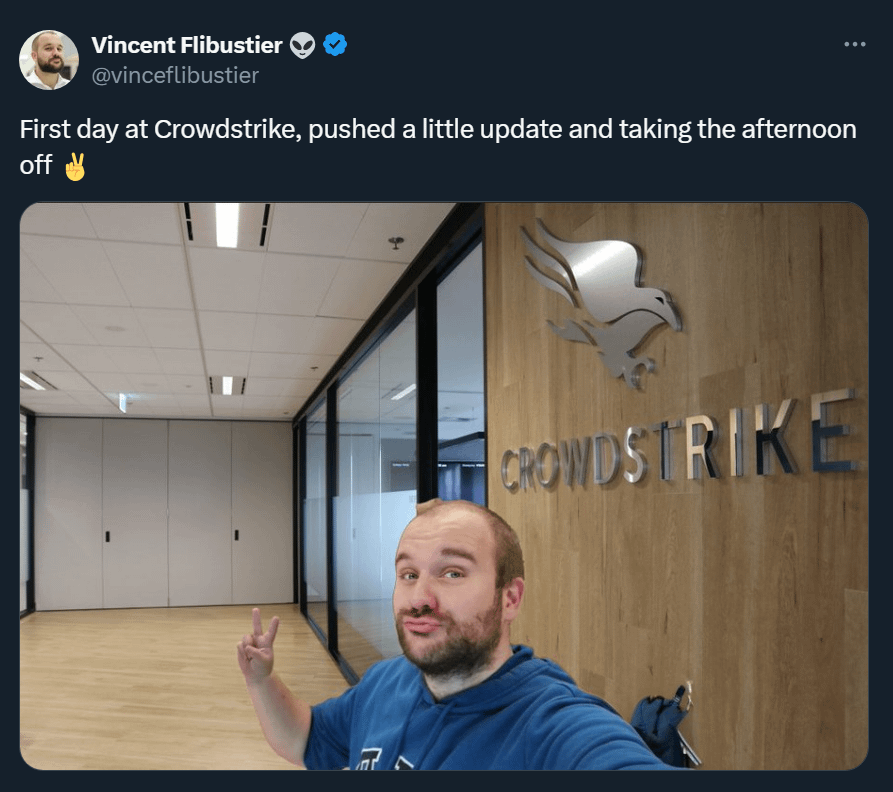
Programmer Humor
18532 readers
2245 users here now
Welcome to Programmer Humor!
This is a place where you can post jokes, memes, humor, etc. related to programming!
For sharing awful code theres also Programming Horror.
Rules
- Keep content in english
- No advertisements
- Posts must be related to programming or programmer topics
founded 1 year ago
MODERATORS
1
2
3
4
5
6
7
8
9
229
Quantum Lock suspends sales due to developers losing access to source code
(store.steampowered.com)
10
11
12
13
14
15
16
17
18
19
21
22
23
24
25
view more: next ›