What's the deal? I'm testing using https://coveryourtracks.eff.org Is it truly unique (and repeatable), or is it perhaps being randomized on every request?
I've tried normal Firefox, Mull, and IronFox. With and without jShelter.
I'm using my phone. Stock Android on a Pixel 7 Pro.
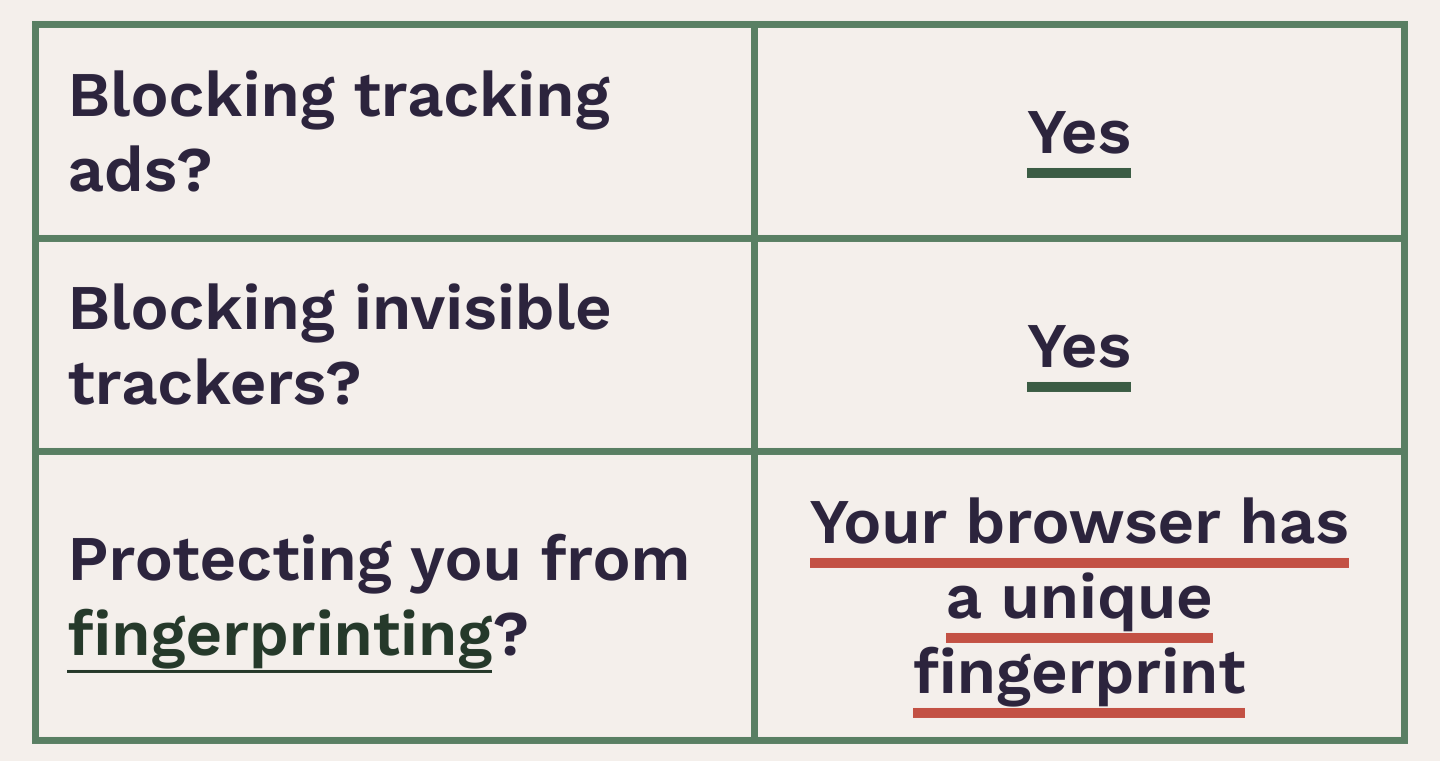
In DDG Browser I have a "nearly unique" fingerprint.
I installed CanvasBlocker and disabled privacy.resistFingerprinting in IronFox (since CanvasBlocker said to), and my fingerprint is still unique. I guess I'm not surprised since I think CanvasBlocker is designed to randomize canvas fingerprinting.
Any tips on having even a shred of privacy when browsing the web on Android?
Update
The biggest identifying characteristics are screen size and user agent. User agent can be faked with an extension. I can't exactly change my screen size.
I don't know what exactly what I did, but I managed to improve to "nearly unique" in IronFox. I think all I did was install Cookie Autodelete. It's an extension I've used for a long time in Mull, and finally got around to installing it. Then I installed "User-agent Switcher" and chose a Chrome user-agent and now I'm back to "Unique". 🤔
EFF mentioned Tor Browser having some other best anti-fingerprinting, so I tried installing that. "Unique Fingerprint". Again, maybe that's fine if it means it's randomized on every request. Does anyone know if that's the case? If part of the fingerprint is a hash of canvas data and WebGL data, etc. Then I can easily see your fingerprint being unique if a browser or an extension is intentionally fuzzing that data.
Update 2
I tried Fennec with just jShelter, uBlock Origin, and Cookie AutoDelete (not that I think those last two matter).
Obtained a "randomized fingerprint" result. Success?
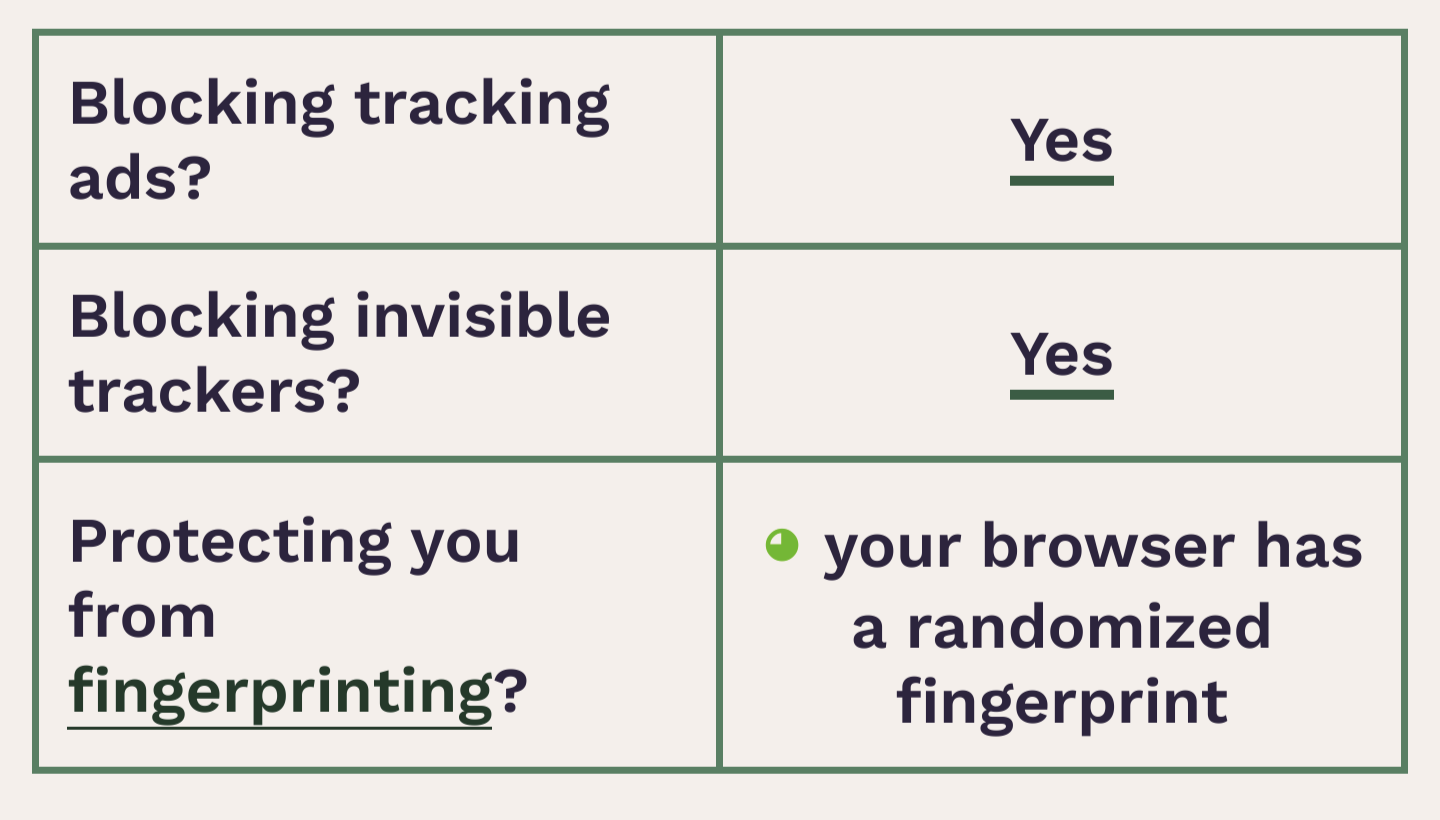

I've done that, and it's a little of everything. The page doesn't offer any advice on how to address anything.
The biggest ones are screen size and user agent. User agent can be faked with an extension. I can't exactly change my screen size.
I don't know what exactly what I did, but I managed to improve to "nearly unique" in IronFox. I think all I did was install Cookie Autodelete. It's an extension I've used for a long time in Mull, and finally got around to installing it. Then I installed "User-agent Switcher" and chose a Chrome user-agent and now I'm back to "Unique". 🤔
For the screen size, it's not actually the screen but the window, which is why tor browser opens in a fixed window size. If you just maximize, even though many use 1080p monitors, your particular settings of your DE give you away (size of bars, window decorations, ...)
I'm on mobile.
Ah sorry, missed that, yeah mobile screens are kind of identifying, not sure if any browsers get around that
What about popup view? If you change the window size every now and then it should be safe I assume.
Cromite manages to randomize it for me in such a way that it's different every time I check, but I never notice anything myself
I suspect they're multiplying all of the 1-in-X probabilities, and if they come up with less than 1-in-8 billion, then they call that unique. If they were actually comparing your values against a hash of previous visitors, then the second time you visit, you'd no longer be unique.
eta: screen size and various hardware measures are probably the lowest probability fingerprints, but they're all highly correlated - there's a few million Pixel 7's out there, but you've probably got like 1-in-1000 screen size and a couple other 1-in-500+ hardware, and that would push you to "1-in-billions," even though there's millions of people with the same fingerprint.
The user agent string from each browser
The HTTP ACCEPT headers sent by the browser
Screen resolution and color depth
The Timezone your system is set to
The browser extensions/plugins, like Quicktime, Flash, Java or Acrobat, that are installed in the browser, and the versions of those plugins
The fonts installed on the computer, as reported by Flash or Java.
Whether your browser executes JavaScript scripts
Yes/no information saying whether the browser accepts various kinds of cookies and "super cookies"
A hash of the image generated by canvas fingerprinting
A hash of the image generated by WebGL fingerprinting
Yes/no whether your browser is sending the Do Not Track header
Your system platform (e.g. Win32, Linux x86)
Your system language (e.g. en-US)
Your browser's touchscreen support
For me only one parameter was an outlier, so I assumed that you would see something similar...