Techbros are incompetent?! Who knew.
Not The Onion
Welcome
We're not The Onion! Not affiliated with them in any way! Not operated by them in any way! All the news here is real!
The Rules
Posts must be:
- Links to news stories from...
- ...credible sources, with...
- ...their original headlines, that...
- ...would make people who see the headline think, “That has got to be a story from The Onion, America’s Finest News Source.”
Comments must abide by the server rules for Lemmy.world and generally abstain from trollish, bigoted, or otherwise disruptive behavior that makes this community less fun for everyone.
And that’s basically it!
Can’t move fast and break things with things that aren’t broken.

Techbros + government bureaucracy
What could go wrong
Competent employees are expensive and don't support the administration's goals.
Oooh that's juicy. I wonder how many holes they left in the important production systems that they've been touching.
I also wonder, with how progressive and dissenting American programmers and cybersec experts are, if our l33t h4x0r sk1llz could be turned against DOGE?
Not suggesting anything wildly destructive, just some friendly grey-hat trolling to slow them down and expose their flaws. Think of it as a complimentary pen-test.
Part of me also thinks they are hoping some people will slip in some "proof" of fraud somewhere, like how people "proved" the COVID vaccine was killing people via VAERS.
I also wonder, with how progressive and dissenting American programmers and cybersec experts are, if our l33t h4x0r sk1llz could be turned against DOGE?
What can hurt Musk? These kids are nobodies, his co-conspirators all depend on his will, and the only thing I suspect is probable to crush him is either a lone gunner or an oil\tech barron who got too pissed of from his plans ruining their business prospects.
Anyone with a gun and a brain.
Yes. But how?
Here's an archived version of the article to get past the paywall. The hackers went to the network tab of their browser's developer console and noticed that the API calls to write to the database weren't password protected.
Literally the dumbest shit I've ever heard of. Why is this man still alive?
What the actual fuck 😂😂😂😂
Compared with an SQL injection, how sophisticated is this method?
If SQL injection is picking a lock, this is entering through an unlocked door.
Not sophisticated at all, authentication on API routes is way earlier on the security checklist than SQL query sanitisation. This site is amateur work.
Much much simpler, with a SQL injection at least you have to bypass the filters set, this is just submitting the changes through an API and the DB just eats it up.
SQL injection is like this: you have something you can interact with on the browser like a form containing different values.
You hit a button and that value is sent and merged into a SQL query.
Say the value is an user ID and you're deleting an account, perhaps your own.
If the coder is incompetent the API will run this query: "DELETE FROM USERES WHERE ID = "
Which means that if you open the developer console, change the value field for that html ID you can break that SQL line and write more SQL, or you can delete other users based on their ID.
Essentially editing a frontend input allows that input to be ran directly by the SQL engine. It's like having full access.
So through that ID field you can inject more SQL code. There's multiple ways to do this, sometimes the URL itself on a website uses these query parameters like "&search=something” and the "something" is injected into the SQL string.
SQL injection is baby's first exploit, this method is like granting everyone DB access.
Not to worry, they don’t use SQL
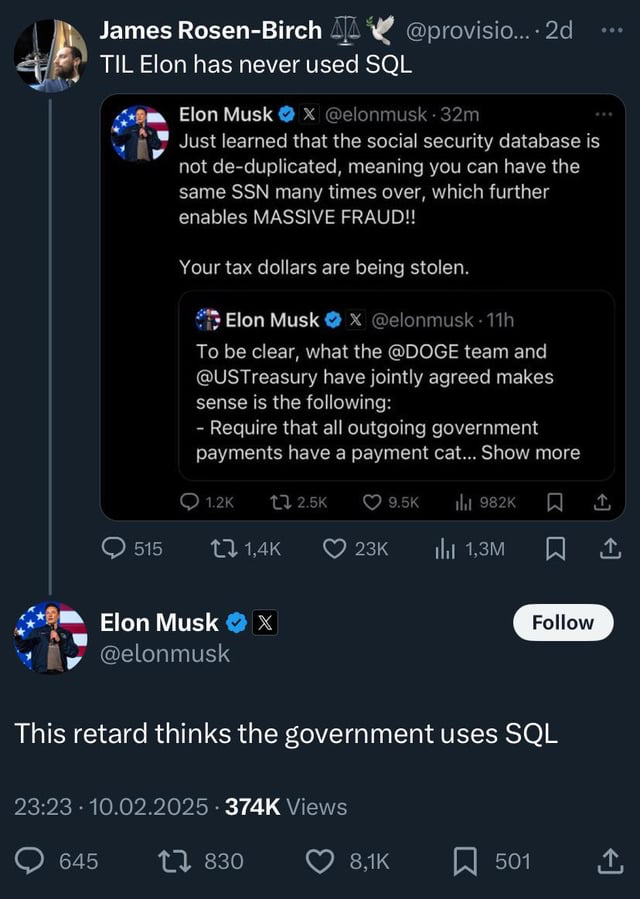
I'm not an expert, but it sounds comparable.
SQL injection is like picking a lock.
This is like trying to open the door and finding out there's no lock.
The door isn't necessarily obviously visible, but most buildings do tend to have doors.
Borrowed and expanded upon another commenter's metaphor
HOLY GUACAMOLE WOW
Ah, unfortunately this is only accessible by master-level bitwizards in the discepline of hacking.
Even more unfortunate is that discerning the 'how' is only accessible by those who are adept at reading the article.
Can or could?