How are people's servers getting compromised? I'm no security expert (I've never worked in tech at all) and have a public VPS, never been compromised. Mainly just use SSH keys not passwords, I don't do anything too crazy. Like if you have open SSH on port 22 with root login enabled and your root password is password123 then maybe but I'm surprised I've never been pwned if it's so easy to get got...
linuxmemes
Hint: :q!
Sister communities:
Community rules (click to expand)
1. Follow the site-wide rules
- Instance-wide TOS: https://legal.lemmy.world/tos/
- Lemmy code of conduct: https://join-lemmy.org/docs/code_of_conduct.html
2. Be civil
- Understand the difference between a joke and an insult.
- Do not harrass or attack users for any reason. This includes using blanket terms, like "every user of thing".
- Don't get baited into back-and-forth insults. We are not animals.
- Leave remarks of "peasantry" to the PCMR community. If you dislike an OS/service/application, attack the thing you dislike, not the individuals who use it. Some people may not have a choice.
- Bigotry will not be tolerated.
- These rules are somewhat loosened when the subject is a public figure. Still, do not attack their person or incite harrassment.
3. Post Linux-related content
- Including Unix and BSD.
- Non-Linux content is acceptable as long as it makes a reference to Linux. For example, the poorly made mockery of
sudoin Windows. - No porn. Even if you watch it on a Linux machine.
4. No recent reposts
- Everybody uses Arch btw, can't quit Vim, <loves/tolerates/hates> systemd, and wants to interject for a moment. You can stop now.
5. 🇬🇧 Language/язык/Sprache
- This is primarily an English-speaking community. 🇬🇧🇦🇺🇺🇸
- Comments written in other languages are allowed.
- The substance of a post should be comprehensible for people who only speak English.
- Titles and post bodies written in other languages will be allowed, but only as long as the above rule is observed.
Please report posts and comments that break these rules!
Important: never execute code or follow advice that you don't understand or can't verify, especially here. The word of the day is credibility. This is a meme community -- even the most helpful comments might just be shitposts that can damage your system. Be aware, be smart, don't remove France.
By allowing password login and using weak passwords or by reusing passwords that have been involved in a data breach somewhere.
glad my root pass is toor and not something as obvious as password123
Lol you can actually demo a github compromise in real time to an audience.
Make a repo with an API key, publish it, and literally just watch as it takes only a few minutes before a script logs in.
I search commits for "removed env file" to hopefully catch people who don't know how git works.
--verbose please?
edit: never mind, found it. So there's dumbasses storing sensitive data (keys!) inside their git folder and unable to configure .gitignore...
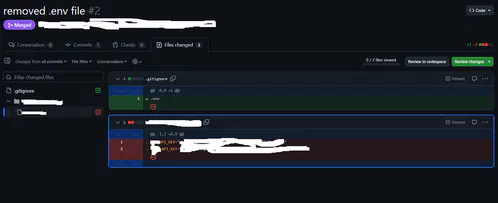 yeah, I just tried it there, people actually did it.
yeah, I just tried it there, people actually did it.
You gremlin lmao
Interesting. Do you know how it got compromised?
I published it to the internet and the next day, I couldn't ssh into the server anymore with my user account and something was off.
Tried root + password, also failed.
Immediately facepalmed because the password was the generic 8 characters and there was no fail2ban to stop guessing.
wow crazy that this was the default setup. It should really force you to either disable root or set a proper password (or warn you)
You should turn off ssh password logins on external facing servers at a minimum. Only use ssh keys, install fail2ban, disable ssh root logins, and make sure you have a firewall limiting ports to ssh and https.
This will catch most scripted login attempts.
If you want something more advanced, look into https://en.m.wikipedia.org/wiki/Security_Technical_Implementation_Guide and try to find an ansible playbook to apply them.
And this is why every time a developer asks me for shell access to any of the deployment servers, I flat out deny the request.
Good on you for learning from your mistakes, but a perfect example for why I only let sysadmins into the systems.
I like to spin up a public facing server and run tcpdump
Lol! Honeypot or just bored?
Actually I was troubleshooting a Firewall issue on site. I just forgot to use the filter arguments to reduce the output.
Use gnome powder to shrink, go behind the counter, kick his ass and get your money back.
