this post was submitted on 28 Sep 2023
323 points (75.7% liked)
Games
33730 readers
890 users here now

Welcome to the largest gaming community on Lemmy! Discussion for all kinds of games. Video games, tabletop games, card games etc.
Weekly Threads:
Rules:
-
Submissions have to be related to games
-
No bigotry or harassment, be civil
-
No excessive self-promotion
-
Stay on-topic; no memes, funny videos, giveaways, reposts, or low-effort posts
-
Mark Spoilers and NSFW
-
No linking to piracy
More information about the community rules can be found here.
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
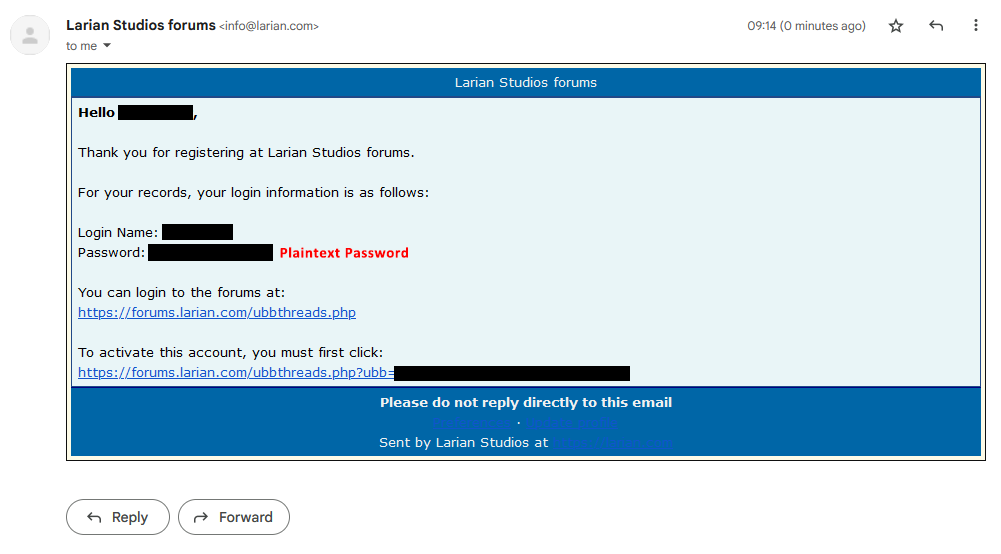
It's possible that this email is a result of forum user creation, so during that submission the plaintext password was available to send to the user. Then it would be hashed and stored.
I don't know why you'd give them any benefit of the doubt. They should have already killed that with this terrible security practice.
But yeah, sure, maybe this one giant, extremely visible lapse in security is the only one they have.
I'm just explaining how user authentication works for most web applications. The server will process your plaintext password when your account is created. It should then store that as a hashed string, but it can ALSO send out an email with that plaintext password to the user describing their account creation. This post does not identify that passwords are stored in plaintext, it just identifies that they email plaintext passwords which is poor security practice.
This particular poor security practice is very much like a roach. If you see one you have a bigger problem.
See, I can also repeat myself as though you didn't understand the first time.