Tanders
That certainly is putting the IDP back in Magic 👍
TL;DR: Yes, ISO 2700{1,2} are a low barrier of entry but a common set of controls that should be able to be applied anywhere.
The biggest hurdle to deploying any framework is updating the cycle of controls and keeping them aligned both with management and with the parties implementing them. There is as much non-infosec work as there is actual implementation of the controls.
- Policy Statement: Management guideline / statement to be followed
- Process: The flow to follow in order to meet that policy statement
- Procedure: The steps to follow in order to enable the process
- Standard: The measurement of the compliance with the policy statement
Each one of the (Annex A) 14 domains has specific controls within the ISMS (27001) that each need the above implementation steps in a big ol' spreadsheet. Then the technical controls within ISO 27002 need to be applied, documented, and supporting evidence gathered as well.
For implementing ISO 27002 I'd highly recommend looking at Common Criteria or the CIS controls that map 27002 to CIS.
I usually have them coarsely ground for my french press. I've had the Volcania ones and it felt like they were coated with something.

I had some servers sitting around from a previous project and I put them to use.
As soon as I wanted a valid TLS endpoint I was going down the rabbit hole of tunneling the local services; ingress or egress I'd have "trust issues" that I would have to deal with such as where the vaults live and get the database to them, sshfs? zfs smb? nfs? So I decided to extend out for the public services and keep the private services a couple tunnels away from the internet.
The other nice part is that I can make a tmpfs/memfs mount for my vault and cache it at the edge, still working on that one. ;-)
I've been working on a locally hosted instance of VaultWarden, deploying it locally is easy with Alpine but I want it accessible remotely. That requires some restructuring and trust. OpenBSD.Amsterdam is a good choice for that, a small instance of theirs works as my front end relaying to a system that connects over WireGuard to my local VW install with PGSQL back-end.
Presently my solution is 1P/BW for low value accounts, but a VaultWarden on a USB Armory Mk II for high value. The Somu works great for storing keys to open the VW vault. Overkill but it was fun to make.
(Testing multiple images)
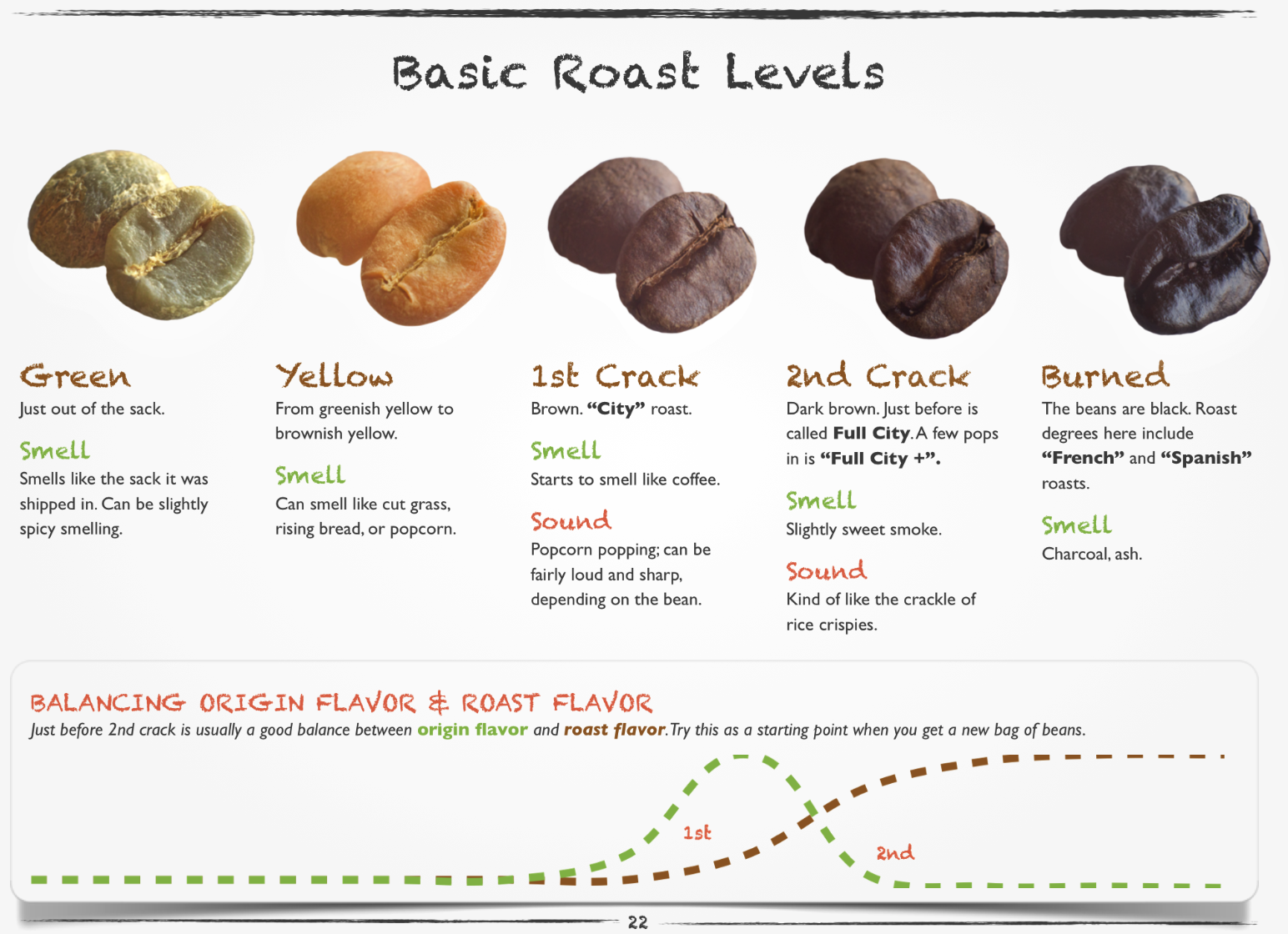
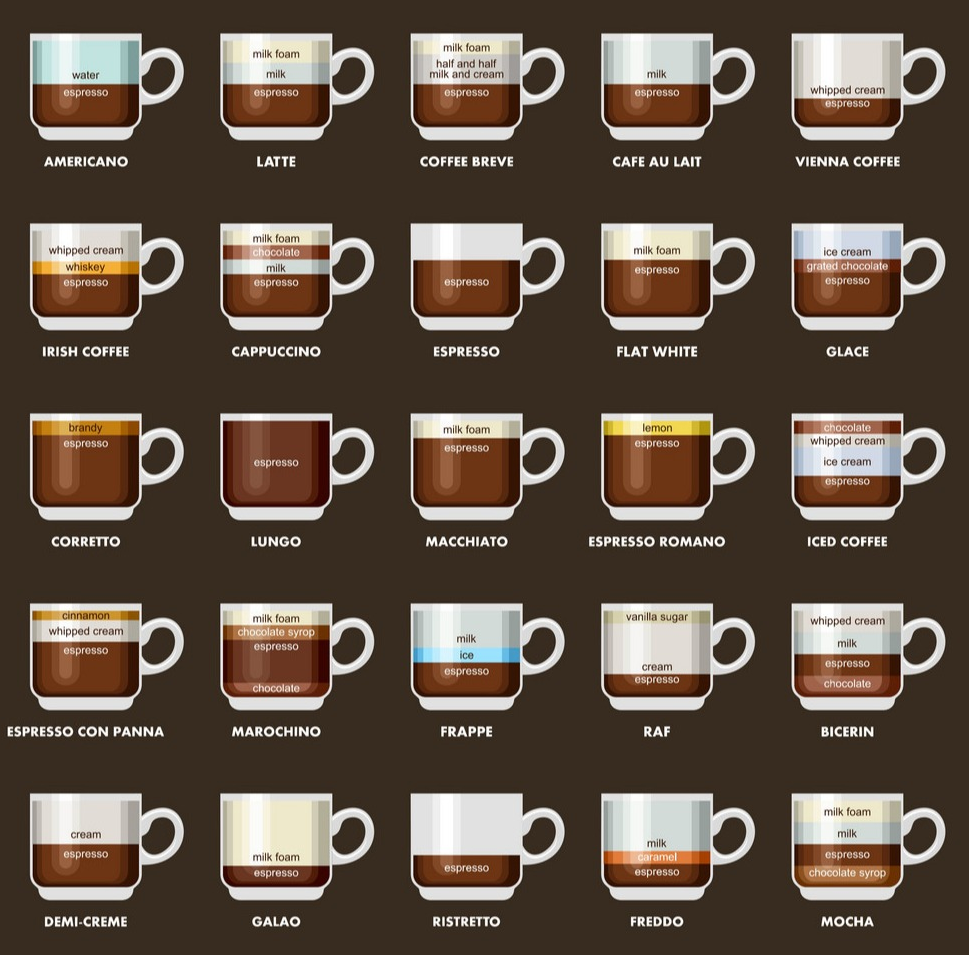
A few considerations: the bean type, the roast type, and the creation of the final drink.