I'm trying to block the most likely attack vectors which is definitely VPS providers at this point in time. I just figure if I am blocking subnets plus additionals I identify it will force them out of these vectors to attack in ways I might be able to report better abuse.
Here check out my analysis.
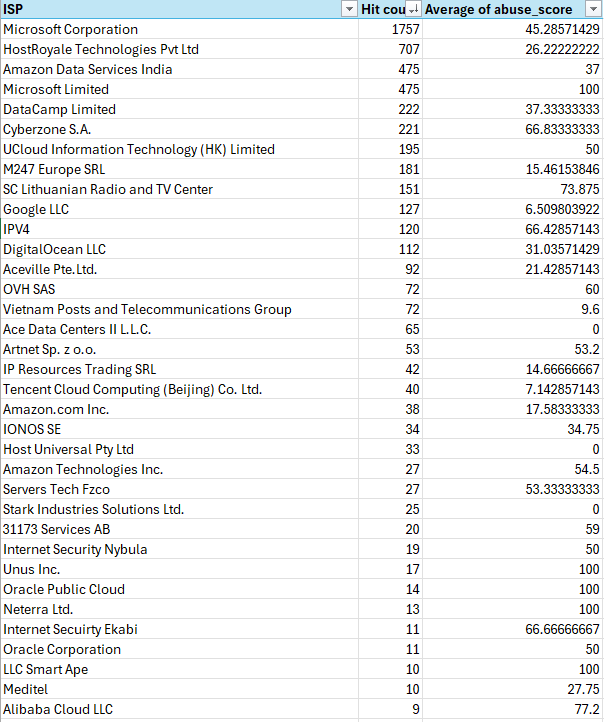

You're going to have to read every single release with breaking changes.