The website requests an image or whatever from 27748626267848298474.example.com, where the number is unique for the visitor. To load the content the browser has to resolve the DNS for it, and the randomness ensures it won't be cached anywhere as it's just for you. So it queries its DNS server which queries your DNS provider which queries the website's DNS server. From there the website's DNS server can see where the request came from and the website can tell you where it came from and who it's associated with if known.
Yes it absolutely can be used for fingerprinting. Everything can be used for fingerprinting, and we refuse to fix it because "but who thinks of the ad companies???".
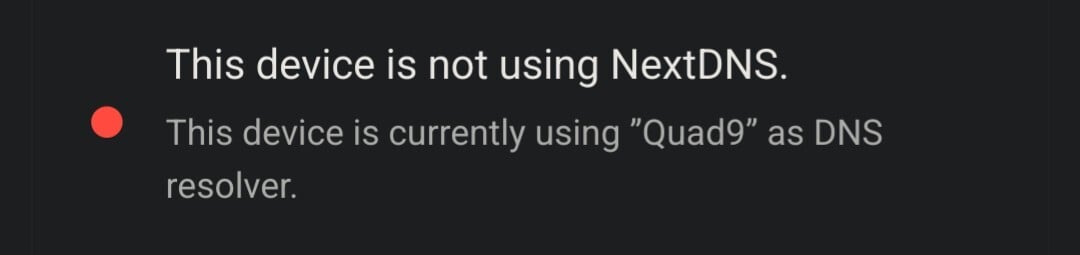 When I tried changing private DNS to Cloudflatein settings it instantly showed my new resolver.
But how exactly it works? Does the browser send used DNS server to website? Or it is done somehow via JavaScript?
And also: So every website can know what I am using now? Can it be used for fingerprinting?
When I tried changing private DNS to Cloudflatein settings it instantly showed my new resolver.
But how exactly it works? Does the browser send used DNS server to website? Or it is done somehow via JavaScript?
And also: So every website can know what I am using now? Can it be used for fingerprinting?