this post was submitted on 19 Dec 2023
1598 points (98.0% liked)
memes
10648 readers
3149 users here now
Community rules
1. Be civil
No trolling, bigotry or other insulting / annoying behaviour
2. No politics
This is non-politics community. For political memes please go to [email protected]
3. No recent reposts
Check for reposts when posting a meme, you can only repost after 1 month
4. No bots
No bots without the express approval of the mods or the admins
5. No Spam/Ads
No advertisements or spam. This is an instance rule and the only way to live.
Sister communities
- [email protected] : Star Trek memes, chat and shitposts
- [email protected] : Lemmy Shitposts, anything and everything goes.
- [email protected] : Linux themed memes
- [email protected] : for those who love comic stories.
founded 2 years ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments
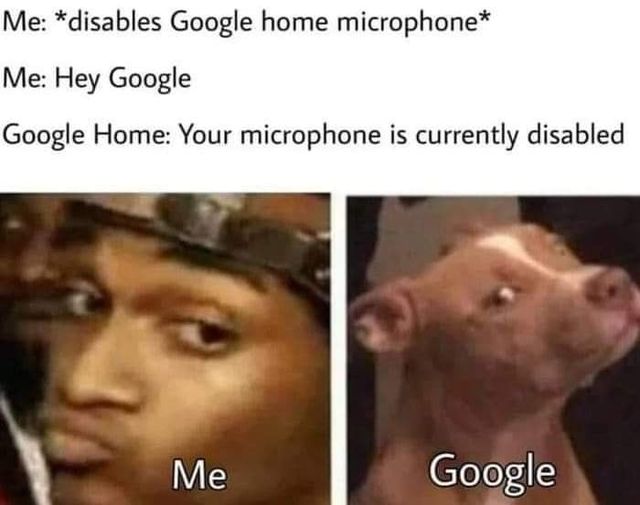
Want an honest answer?
Onboard are >=2 bits of code. At least one of those is a specific system trained to recognize a "wake word". This specific system (ostensibly) doesn't send anything to an outside party. Its entire job is to recognize one wake phrase: Alexa, Ok Google, or Siri, and then if that wake phrase is used it responds and tells the second system to listen. As you can imagine, this is a pretty easy job to get right 80% of the time. So that can be put on a chip. So then it does its job, and it's the second system that sends everything to an internet service for whatever reason.
I didn't ask for honesty!
I'd love to have this properly audited sometime. I'd slap like to think that we're generally protected from big companies doing unethical and unjust things to us, by law, ... but nah
(That's not to say I don't believe this explanation; the second half of my comment was just an addendum.)
why is this downvoted? you cant prove its not, if its proprietry. and since the companies listening just happen to profit off data collection (and break/bend the law often), its safe to assume they do this.
Because you can prove it by monitoring network requests with a packet sniffer, which has been done.
Interesting. I haven’t seen this myself but it wouldn’t really surprise me.
It's a standard tactic for people who do networking things
Yeah. I work in that general field but not at the user level like that so never got into packet sniffing. Now’s as good a time as ever eh?