privacy
31 readers
1 users here now
Rules (WIP)
- No ad hominem allowed
- Attack the idea, not the poster
founded 1 year ago
MODERATORS
1
2
3
4
5
6
7
8
9
0
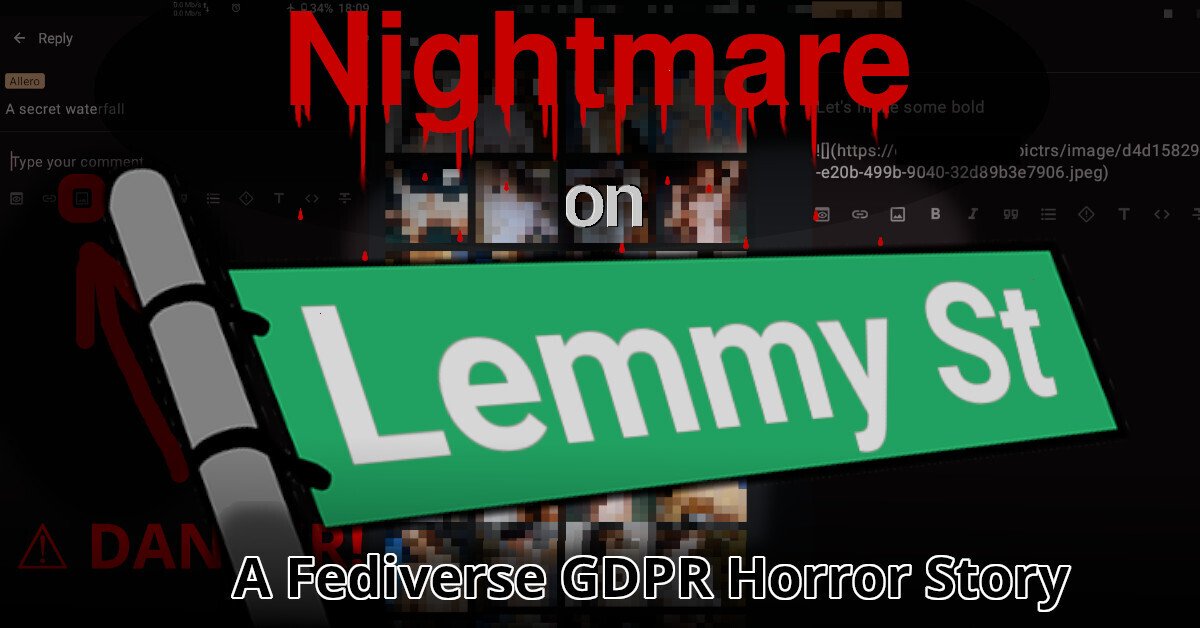
PSA: you can't delete photos uploaded to Lemmy. So don't (accidentally) upload a nude. That would be bad 😱
(tech.michaelaltfield.net)
11
12
13
15
16
17
18
16
Ten years from Snowden revelations – what’s next for Tor and privacy online? | Tor Project
(blog.torproject.org)
19
20
6
Four more months of Section 702 snooping slipped into $890B US defense budget bill
(www.theregister.com)
21
22
23
24
25
view more: next ›